How to turn on 'monitor mode' and decrypt 802.11?
Hello,
I'm a total packet sniffing newbie. I've read most of the relevant wiki pages on setting up the 4-way handshake that's required (password:SSID in IEEE 802.11 settings) to decrypt 802.11 packets but I can't see any such handshake taking place. I have not been able to find any of the reported "monitor mode" settings. I have a whole slew of packets captured that are encrypted that I'd like to see the contents of.
I'm running macOS Mojave 10.14.3 on an intel iMac circa 2014. My wireless router (en0) is an Airport Extreme circa about 2010.
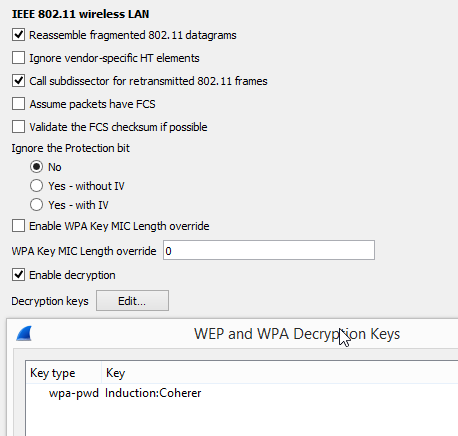
For the sake of argument, my WiFi password is "password" and the network name is "My Home Network" with spaces and all (not sure if spaces are allowed in the wpa-pwd key settings). I entered "password:My Home Network" and clicked ok, but I can't see any decrypted http packets or anything noticeably different. I definitely don't see the 4-way handshake happening in the capture.
Furthermore I'm wanting to capture packets sent to and from a specific Mac device with the address 36:56:9C:4D:4C:5C across the span of an entire day. Any way to limit captures to only that device would be helpful as I'd like to keep the file size down.
Any ideas what settings I may be missing or have screwed up?
What info am I leaving out? Sorry for my novice-ness, and thanks in advance!

Sorry. Is this a dumb question or is there not enough info to warrant a response? I'm hoping for someone to help me troubleshoot the reason I can't get monitor mode running to see unencrypted packet data on my own network.
Can I suggest this tool for a mac:
https://www.adriangranados.com/apps/airtool
You say that you have packets captured but don't know how to set monitor mode... so without seeing what they are, we don't know what the problem is. You may have 802.11 frames already; you may not. If not, you likely won't see the EAPOL frames and decryption is not useful anyway.
So start from the basics - try that tool; post a capture so we know what you are getting and can then guide you. There are techniques to force devices to generate EAPOL key frames: remove it from the AP either at the AP or just reboot the device (or AP). But no point in doing this until you are in position to capture them.
Suggestion: Don't worry about long term capture until you get the short term capture sorted ...(more)
You'll only see the handshake if it takes place while you're capturing. As the Wireshark Wiki page on decrypting 802.11 says, "In order to capture the handshake for a machine, you will need to force the machine to (re-)join the network while the capture is in progress." "The machine" here refers to the machine whose traffic you're trying to capture (not to the machine running Wireshark). Did you try that?
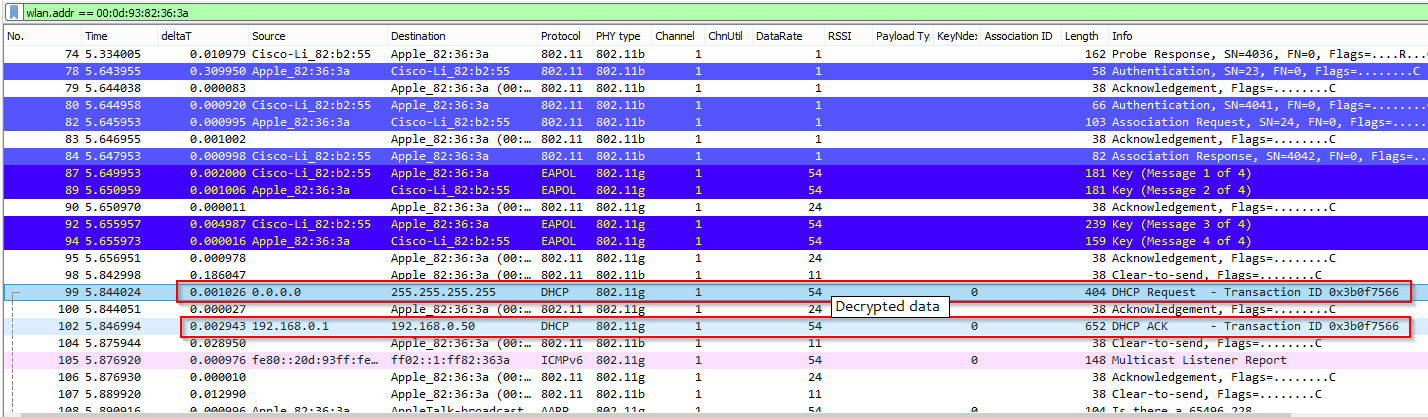
Thanks for the replies! I captured a bunch of packets via wireshark and have posted the .pcap file here. I ran this capture on my iMac, and I re-joined the en0 network on my iphone to try and see the 4-way handshake during the capture but I don't see it. Maybe I'm misunderstanding how I'm supposed to re-join the network.
With the trace we can tell that you are capturing traffic in monitor + promiscuous mode; this is a good start. I see eapol frames - try this display filter:
Frames 549,555, 557, and 559 are for an apple device with an apple BSSID; both are consistent with your comments that it's an iphone and the AP is an apple airport. If you want to try decryption, now that you have the eapol frames, it should work. Note that the SSID contains spaces, so not sure how they will work if you just enter that into the passphrase/SSID field; you may need to precompute the PMK via a site such as
https://www.wireshark.org/tools/wpa-psk.html